When 2-factor authentication (2FA) is combined with password managers like 1Password and LastPass, it can help people securely access their personal and work accounts, and make it more difficult for hackers to breach private data. But those taking advantage 2FA often use the most insecure version of it — such as email and SMS-based codes that hackers can acquire with ease.
Although 2FA raises the barrier to account access with another step of identity verification, it is not a replacement for actual account security. The entire 2FA space is fraught with loopholes for hackers to exploit.
Anyone can bypass 2FA.
2FA hasn’t magically stopped hackers from breaching SaaS accounts once and for all, partly because it has to be friendly enough for public adoption. At the same time, hacker ingenuity continues to exploit 2FA’s weak spots.
2FA’s emphasis on customer experience creates gaping vulnerabilities.
Customers demand features for convenient account access in the event that 2FA is cumbersome, and password recovery options for when they experience issues — such as a lost or broken phone, or a hardware authentication key that stopped working. But these account recovery options render even the most stringent forms of 2FA (like hardware-based authentication tokens) completely useless.
2FA providers simply can’t deny users the options of remembering devices or authenticating accounts in other ways because of the simple truths that people are in a hurry and they forget things.
2FA providers also allow users to add trusted devices that don’t require ongoing verification after initial approval. But tying identity to a device is inherently insecure: what if the device is lost or compromised? This feature undermines what should be the very essence of 2FA — trust no one and trust no device without further proof of identification.
Brute force bypass of 2FA
Hackers can steal authentication codes using brute force. Although many services will block users from logging in after a certain number of attempts, some don’t have limits, or they just allow attempts after certain time interval has passed. (For example, Slack lets you try 20 codes before sending a password reset to your email.)
The length of a typical numerical 2FA code is 4 to 6 characters, meaning that there are roughly 151,800 possible codes for the hacker to input using an automated computer program. Increasing the length of 2FA codes to 15 numbers would make brute force bypasses more difficult, but would inconvenience users who might have a hard time remembering the seemingly endless stream of numbers.
Spoofed 2FA login pages
Hackers create spoofed login pages to phish unsuspecting victims into surrendering their credentials and one-time 2FA code. When the victim enters their SMS-based, email-based, or authenticator app-based code into the login page, the information is forwarded to the hacker, who then enters it onto the actual login page to access the desired account.
Servers can automate this process, making these attacks less targeted, but just as effective if the look and feel of the spoofed login page approximates the login page that customers are familiar with and trust. 2FA is completely defenseless against impersonation attacks. This is why anti-phishing software is needed to identify fraudulent webpages.
Ranking the security of 2FA from worst to best
Although 2FA has evolved beyond security questions about the name of your first pet, it still has a long way to go in terms of becoming efficient and convenient enough for widespread adoption.
Many globally-recognized companies, such as Netflix, Hulu, and Spotify, still have no 2FA methods in place for customers to use. The website Two Factor Auth shames companies like those which don’t support 2FA, and lets consumers know what services do and don’t provide 2FA for added security.
There are several forms of 2FA to take advantage of, but it’s important to know that some are fundamentally flawed.
5. Email code (most insecure)
Email-based 2FA works when the account provider sends the user a 5-10 digit alphanumeric token via email that they then input into the login page. A compromised email account or a spoofed account login page can render this method completely useless.
4. Phone-based authentication (code sent via SMS or phone call)
Phone-based methods of 2FA are slightly more difficult to intercept than email-based 2FA, but are still very vulnerable because so much of our identity is tied to our phones.
Lately, there have been multiple reports on the vulnerabilities of SMS-based 2FA. A little bit of social engineering is all it takes to trick mobile carriers like AT&T and Verizon into transferring a SIM card or phone number onto a hacker’s device. If hackers don’t feel like picking up the phone to deceive mobile carriers, they can find a way to get the victim to install malware that forwards all text messages (including those with the authentication code) to a device of their choice. Even simpler, they can just lead the user to a spoofed login page that captures phone-based 2FA codes.
3. Authenticator apps
Phone-based apps like Google Authenticator generate one-time passwords that expire at predetermined intervals. These time-based codes constantly rotate through the app, regardless of if the user needs them or not.
Authenticator apps are vulnerable to breaches, but so far, none have happened. They are also susceptible to brute force attempts, but the expiration of codes makes this extremely difficult. A lost device is the most likely way that an authenticator app and its codes could be compromised.
2. Security keys / universal 2nd factor
Hardware-based Yubikeys and other universal 2nd factor devices are a reaction against the insecurity of the cloud, where data can be remotely accessed by anyone. The logic is that if there is only one unique key, then in theory, accounts protected by it are unhackable. This is not the case.
Users plug these “keys” into computers like USBs, and then tap them with their finger to authenticate the application they’re trying to access. (The tap doesn’t scan for fingerprints — it’s just part of the product’s tactility.) Like magic links sent to email accounts, universal 2nd factor is also considered a form of passwordless authentication.
Unfortunately, security keys can be bypassed if the hacker simply forwards a password reset link, or chooses another mode of 2FA. Many customers experience issues with their hardware key, which is why 2FA providers who support them have to provide other methods of authentication in the event that it’s not working, or that the user is confused. Hardware keys are only ideal when they work, and when the user configures their account so that other account recovery options are not available at login.
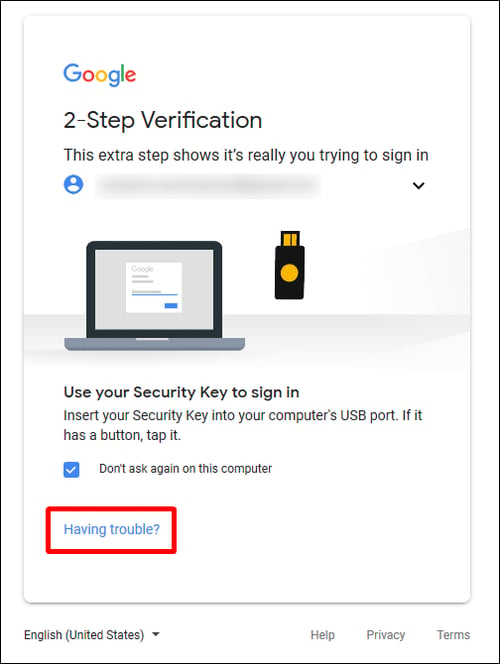
Hardware-based authentication tokens (shown in the image above) are touted as the most difficult to bypass form of 2FA, but most SaaS accounts offer users alternative options in case they experience difficulties.
Hardware keys are only ideal when they work, and when the user configures their account so that other account recovery options are not available at login.
1. Biometrics (most secure)
Currently, there is no widespread implementation of biometric-based 2FA on commercially-available devices, despite the fact that most smartphones can capture biometrics. This is because interoperability (between hardware-based devices that capture biometrics and the SaaS apps using them in the cloud) is not optimized, and the technical challenges in overcoming this will take some time.
The most popular online services that use biometric authentication are largely finance or banking apps, like Robinhood or Bank of America. Even so, the risks with biometric-based 2FA are obvious.
If hackers could acquire unique identifiers like retina scans or fingerprints, they could access a wealth of information about that victim. As Roger Grimes warns in ComputerWorld, “once we start storing fingerprints in global identities, attackers who compromise the identity provider will have your fingerprints…forever. They could possibly ‘be you’ on all the other web sites that accept your fingerprints.”
Conclusion
2FA should not be trusted as the final line of defense for authentication, even though it currently is. The immediate challenge is fortifying the 2FA infrastructure so that fewer loopholes exist.
In order to protect online accounts, users should do two things. First, they should rely on password managers to generate complicated passwords that they don’t even have to remember. Secondly, they should ensure that the most secure forms of 2FA are running on their accounts.

Leave a Reply