As a result of the COVID-19 outbreak, cybercriminals increasingly are targeting organizations that now have more remote workers and fewer IT and security staff at the ready to mitigate hacker attacks and intrusions, security experts say.
The disease has led to over 9,500 deaths worldwide, according to a Johns Hopkins University research team.
Here are some takeaways about how attackers are exploiting the crisis and what security teams must do to defend their organizations.
Fresh Opportunities for Criminals
For criminals, this crisis offers a slew of new opportunities, and if there’s one thing we know about cyber adversaries, it’s they’re adaptive and reactive.
When an incident happens that doesn’t involve remote work, you see the attackers moving very quickly to launching phishing campaigns around an ordinary threat or humanitarian disaster. What COVID-19 gives the adversaries is an opportunity both to phish – to sort of weaponize the desire for information – and at the same time a new set of opportunities to target. With all of these people working remotely [both on work and also personal computers], there’s an opportunity to invade home networks and move laterally on those devices.
Suddenly, ensuring older home routers with undated firmware are either upgraded or replaced isn’t just a consumer security problem, but a corporate one.
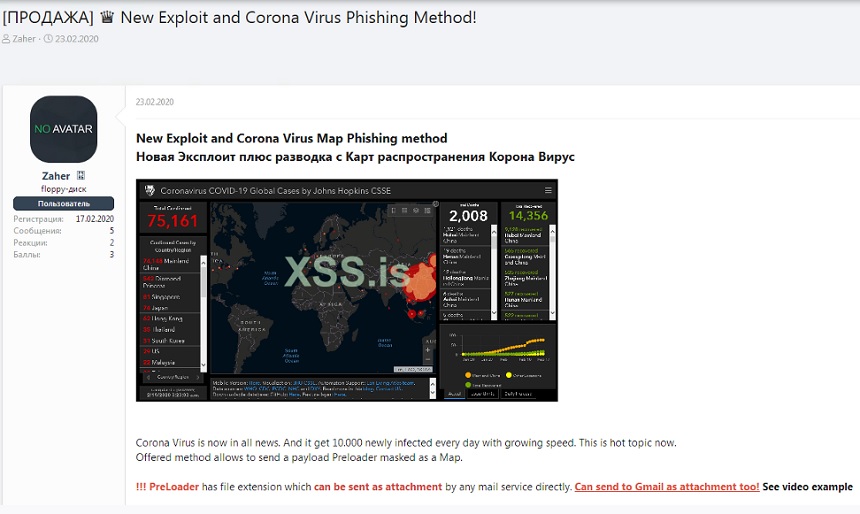
Meanwhile, cybercrime offerings are already available to help criminals perpetrate such attacks. The XSS Russian-language cybercrime forum, for example, is already advertising a COVID-19 themed phishing email kit, priced from $200 to $700, says security firm Digital Shadows.COVID-19-themed phishing kit for sale via XSS.
The kit generates emails that include legitimate, real-time information from the World Health Organization and the Johns Hopkins Center for Systems Science and Engineering, which are both helping to track the spread of the virus, to make them look more authentic and trick recipients into clicking on malicious links they contain.
Target: Home Workers
As the crisis continues, expect to see an increase in the number of cyberattacks on computers, equipment (routers, video cameras), and unprotected home networks used by employees who have switched to remote working due to the spread of coronavirus.
Employees of financial institutions, telecom operators and IT companies are particularly at risk. The goal of cyberattacks will be the theft of money or personal data.
Keep Training Employees
Security experts cite phishing attacks as being one of the biggest threats in this new environment, and warn that existing efforts to safeguard employees are too often inadequate.
Phishing attacks are on the rise, and employees at home might be especially vulnerable. We’ve expressed concerns before that a lot of ‘off-the-shelf’ phishing training is not fit for purpose. It’s important to make sure employees are trained and that they have regular reminders. Organizations using [Office 365] may be especially vulnerable at this time.”
To help, many organizations are releasing materials for free. For example, the SANS Institutehas released large parts of its commercial awareness materials.
But with phishing attacks that prey on coronavirus fears already surging, many organizations are playing catchup.
“Like many phishing scams, these emails are preying on real-world concerns to try and trick people into doing the wrong thing,” the U.K.’s National Cyber Security Center says, noting that shipping, transport and retail industries were being targeted. “Please refer to our guidance on dealing with suspicious emails to learn more about spotting and dealing with phishing emails,” it adds, referring to its latest guidance for keeping employees secure when they work from home.
Target: Malicious Infrastructure
NCSC also says that it’s actively seeking and removing sites and domains that use COVID-19 and coronavirus themes in an attempt to distribute malware or execute phishing campaigns.
“The NCSC has seen an increase in the registration of webpages relating to the coronavirus, suggesting that cybercriminals are likely to be taking advantage of the outbreak,” it says. “These attacks are versatile and can be conducted through various media, adapted to different sectors and monetize via multiple means, including ransomware, credential theft, bitcoin or fraud.”
Criminals Impersonate WHO, CDC
Last month, the World Health Organization warned that criminals have been pretending to be from the organization.
“Criminals are disguising themselves as WHO to steal money or sensitive information. If you are contacted by a person or organization that appears to be from WHO, verify their authenticity before responding,” the organization says.
WHO-themed phishing messages attempt to pressure would-be victims into making poor decisions.
“Do not rush or feel under pressure,” WHO says. “Cybercriminals use emergencies such as 2019-nCov to get people to make decisions quickly. Always take time to think about a request for your personal information and whether the request is appropriate.”
The NCSC also warns: “Cybercriminals have also impersonated the U.S. Center for Disease Control – CDC – [by] creating domain names similar to the CDC’s web address to request passwords and even bitcoin donations to fund a fake vaccine.”
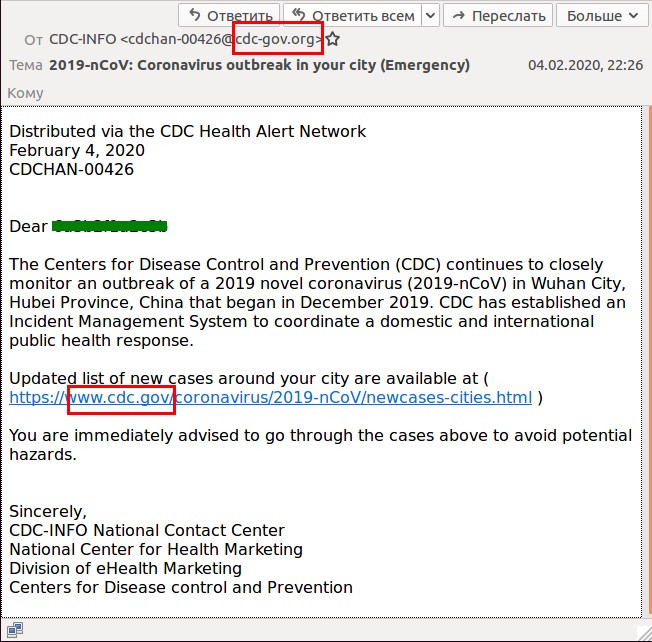
Phishing email disguised as CDC message.
Justice Department Seeks Crackdown
The Associated Press reported that U.S. Attorney General William Barr has instructed the Justice Department to prioritize prosecutions of anyone attempting to impersonate the CDC or WHO, for example, via phishing emails.
But with experts noting that much of today’s cybercrime traces to Russia, which has no extradition treaty with the U.S., it’s unclear how many suspects the FBI and other government law enforcement agencies might actually arrest.
Essential Organizational Defenses
With the sharp rise in employees working from home, numerous cybersecurity experts have urged organizations to ensure they step up their defenses, both for protecting employees as well as protecting the organization and its customers and partners from any insider accounts that attackers might manage to tale over.
As always, backup and recovery plans are essential. “Business continuity is something organizations should constantly test, particularly in healthcare.
Testing your backup and disaster recovery plans is something we should always be doing. But at a time like this where we’re seeing an upswing in malware attacks against hospitals related to coronavirus, and you’re going to have influxes of patients … that puts additional stresses on systems. So it’s definitely a good idea to test and verify that all this stuff works ahead of time.
Home Security Essentials
Essential defenses for at-home workers, meanwhile, include deploying effective anti-virus and email-filtering software and other security software to identify and monitor for unusual activity. IT teams must have sufficient resilience and bandwidth to deal with a wave of IT issues and questions from users. A visible and easy-to-use tool should also be made available to enable staff to report phishing, and there should be regular phishing campaigns and tests to raise awareness. Multifactor authentication is vital for controlling access to important systems and data, too.
Organizations should restrict access to systems via IP blocking to prevent access from countries where the organization does not do business and restrict users’ ability to send mass emails.
Common Sense Still Required
Unfortunately, current levels of anxiety and stress mean that few employees may be thinking clearly, and corporate communications and systems, as well as business processes, may be in disarray. “This makes for an attractive target for misuse, abuse, fraud, scams, phishing or otherwise unauthorized entry to systems by criminals, state actors and [others]. “I’m afraid that the sense of urgency and the feeling but also experience of exceptional measures will only help with scams and fraud.”
Make no assumptions about remote employees’ digital or cybersecurity literacy, warns cybersecurity consultant Jessica Barker, who heads U.K.-based Cygenta, in a blog post devoted to equipping workers to work safely from home.
“For many people now working from home, this may be the first time they have been issued a work laptop or other device for remote working,” she says.
As virus fears continue, cybersecurity is likely not at the top of anyone’s agenda. In addition, remote workers may have trouble differentiating legitimate communications from attack attempts as they struggle to come up to speed on what may be unfamiliar systems.
“Many forced-work-from-home users will find themselves using software they don’t know, as well as less familiar organizational processes”. While unfamiliar technology and services pose a risk, “so do out-of-the ordinary requests” to install new software or click on specified links.
“As organizations move to an increased work-from-home setup, it is now of paramount importance to enforce common sense”.
