Before I get to the device, let me admit to something up front. I’m a computer guy by trade. I’ve installed and/or managed countless PC’s, servers, routers, firewalls, etc in both homes and businesses. I say this to mean that I wasn’t walking into this setup blindly or without a decent understanding of what I was installing, or at least what I thought I was installing. What this also means though is that my home configuration is more like that of a small business with some configuration options that you wouldn’t find in a normal home setup.
So, what is CUJO? As their web site says, “CUJO is a smart firewall that keeps your connected home and business safe from cyber threats so that you can stay secure and private online.” A firewall simply put is a device or software that monitors and filters your network to allow or block specific network communications, or “traffic”. These filters, or “rules”, can be manually configured and, as is the case with Cujo, automatically applied from a central database of known malicious locations. This is a good thing since no single end user is going to be able to constantly assess and identify what the good traffic is vs the bad. CUJO monitors the traffic on your network and sends statistics based on that data to cloud a based database for analysis. If CUJO blocks something, it reports that to the cloud which then updates you via the CUJO phone app. An important note, CUJO never sends the contents of your data, keeping your information private.
The setup process will vary based upon your configuration, and this is of course where it can get tricky. The instruction manual is a foldout sheet with basic diagrams of the “if your setup looks like this, connect it like this” variety. No detailed configuration information. This is probably great for a nontechnical user, but I wanted much more detail. All setup and management functions are handled within the CUJO app (IOS and Android). You should install this first. With that said, CUJO seems to expect that folks will encounter setup problems and offer two methods of gaining help. The Easy way and the Easier way. The Easy way is you call their support number, get a live person on the phone, and they walk you through the setup. The Easier way is you call, make an appointment, and they send someone to your home/office to configure it for you. In home service, wow. In hindsight I probably should have just called them for setup assistance so that I could speak to their level of service, but I took the not-so-easy method and worked my way through configuration. There was some trial and error, but in the end I was able to get everything configured in my non-standard setup.
The app is where everything happens. Setup, monitoring, permissions, it’s all done there. On the main screen you have access to the first 4 primary screens: Home, Devices, Threats, Access, and More.
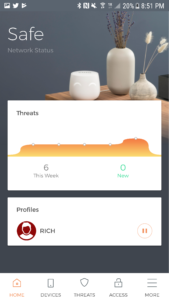
From the Home screen you receive you network status (I’ve only seen Safe), the threat level, and the active Profiles.
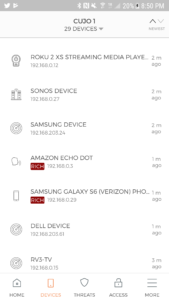
From the Devices screen you’re presented with a listing of all devices that the CUJO has detected on your network. Sometimes it may not know the details on a new device until registered and identified with the cloud, but that usually happens within a day.
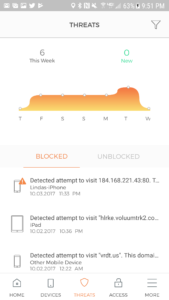
From the Threats screen you have a graph of the threats detected within the last week, whether they were blocked or unblocked, and the specific threats and devices that were affected. You tap on an identified item here to obtain additional details such as the type and classification.
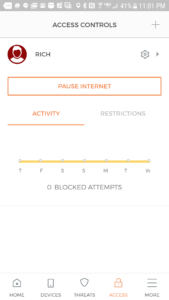
From the Access screen you are presented with the ability to configure specific controls for specific users. You’re also able to monitor and restrict access from here.
All of the screens are easy to navigate and present their respective information clearly. Tap on an item on the Threat screen and you’re shown greater details: The specific threat type, the device that attempted connection,date and time, and if it was blocked or not. Tap on a device and you’re shown the most recent connection date and time, the user profile it is associated with, threats and traffic, and it’s protection status. Dig deeper and you’ll see network specifics and hardware details. These details are pulled from the remote database and are updated as new devices are detected. All of my brand name devices were properly identified.
Cujo is a very transparent device. It just sits there and works. In my family of 5 (26 devices) it picks up less than 10 threats a week on average. All have been browsing links to suspicious sites or those that have been classified as malware. The traffic is blocked and that’s it. No pop ups or notices on the end user side. The only issues that I had was with a gaming device and online play. I needed to allow unprotected access on the XBox 360 for XBox Live to function properly. I did the same for the other consoles in the house even though no one mentioned problems.
For homes and small businesses on a budget, Cujo will provide an additional layer of protection that you should consider.
CUJO Smart Firewall
www.getcujo.com

Leave a Reply